Entrance-running is among the most debated and ethically difficult points in crypto buying and selling. In reality, former Binance CEO Changpeng Zhao (CZ) had lately voiced issues about front-running on DEXs. Whereas the time period originates from conventional finance, the place it’s thought-about unlawful, front-running in crypto has discovered new life on the blockchain in additional advanced and automatic varieties. This text breaks down what front-running in crypto means, the way it works within the crypto area, and how you can keep away from front-running as a dealer.
What Is Entrance-Working? (Conventional Finance vs. Crypto)
In conventional finance, front-running happens when a dealer makes use of data of a shopper’s upcoming massive commerce to position their very own order forward of it, benefiting from the anticipated worth shift. Since this entails insider data and breaches fiduciary obligation, it’s unlawful in most jurisdictions.
However is front-running the identical as insider buying and selling? Not precisely. Whereas each contain unethical behaviour, front-running in crypto usually exploits blockchain transparency. Anybody can view pending transactions within the mempool (reminiscence pool), the place transactions wait earlier than being confirmed. Malicious actors, together with miners, validators, or bots, scan this mempool and submit transactions with increased charges to leap the queue and revenue from worth actions they know are about to happen.
How Does Entrance-Working Work in Crypto?
Blockchain transparency is a double-edged sword. Whereas it ensures belief and auditability, it additionally makes each pending transaction seen earlier than it’s confirmed. Right here’s how front-running works in crypto:
A big commerce is detected within the mempool.
A front-runner submits an identical commerce with the next gasoline price to make sure it’s mined or validated first.
The front-runner earnings from the ensuing worth motion, usually on the expense of the unique dealer.
That is particularly frequent on DEXs the place there aren’t any centralized intermediaries to stop such techniques.
MEV in Entrance-Working
Most Extractable Worth (MEV) refers back to the extra revenue that validators, or beforehand, miners can earn by manipulating the order of transactions inside a block. This manipulation consists of reordering, inserting, and even excluding transactions to maximise positive factors. Initially known as Miner Extractable Worth, the time period has developed with the rise of proof-of-stake (PoS) programs like Ethereum’s, the place block producers are now not miners however validators.
It’s a high-stakes phenomenon that exhibits how revenue incentives can distort truthful transaction ordering.
The MEV ecosystem is a posh enviornment involving a number of gamers. Validators suggest blocks and determine the transaction order. Working alongside them are “searchers” (people or groups that develop refined algorithms to scan public mempools for worthwhile MEV alternatives.) These searchers usually deploy automated bots to behave on their findings in real-time.
These MEV bots function with outstanding velocity and precision, executing methods that exploit worth discrepancies, arbitrage alternatives, and enormous DEX transactions. In lots of instances, they aim so-called “whale” trades or high-volume swaps the place the potential for front-running or sandwich assaults is most profitable. Among the most superior MEV bots have been reported to earn tens and even tons of of 1000’s of {dollars} every month.
Collectively, validators, searchers, and bots kind an intricate worth chain—one which showcases the innovation and equally exposes the dangers related to blockchain transparency.
Widespread Forms of Entrance-Working Assaults
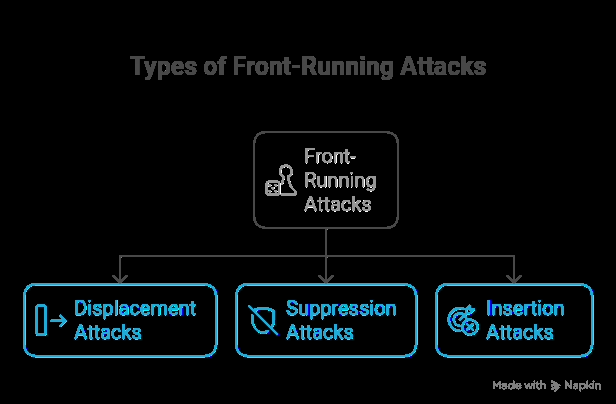
1. Displacement assaults
The attacker observes a pending transaction and submits a competing one with the next gasoline price, pushing the unique transaction again in line. The attacker captures the meant alternative for themselves.
2. Suppression assaults
The front-runner floods the community with high-gas transactions to delay others. This congestion prevents the sufferer’s transaction from being confirmed in time, leading to failed or much less beneficial trades.
3. Insertion assaults (a.ok.a. sandwich assaults)
Among the many most infamous and dangerous types of front-running in crypto is the insertion assault, generally known as a sandwich assault. This tactic entails strategically putting two trades—one earlier than and one after a sufferer’s transaction—in an effort to revenue from the ensuing worth motion.
Right here’s the way it works: A dealer unknowingly submits a big transaction on a decentralized trade, say a purchase order for a particular token. A front-runner, usually an MEV bot or refined dealer, detects the pending transaction within the mempool. The attacker rapidly locations a purchase order simply forward of the sufferer’s transaction, which pushes the token’s worth upward. As the unique dealer’s massive purchase order executes, it does so at this now-inflated worth. Then, nearly immediately, the attacker finalizes the assault by putting a promote order, cashing out on the elevated worth and capturing the distinction as pure revenue.
Right here’s an instance of entrance working: Think about a dealer is seeking to purchase a considerable amount of a DeFi token, say 50,000 models of TokenX, which is presently buying and selling at $2.00 per token. The MEV bot spots this order within the mempool and races to purchase TokenX first at $2.00. This preliminary buy drives the value up barely as a result of token’s restricted liquidity. The dealer’s massive order then will get crammed on the new, increased worth, say, $2.05. Instantly afterwards, the bot sells the identical tokens it purchased earlier at $2.05, making a tidy revenue of $0.05 per token, totalling $2,500, all on the expense of the unsuspecting dealer.
These assaults are notably damaging as a result of they manipulate costs in actual time, damage real customers, and compromise the equity of decentralized markets. Worse nonetheless, since they exploit blockchain transparency and velocity somewhat than hacking or deception, sandwich assaults (a extra superior model of front-running) are troublesome to detect and even more durable to stop with out proactive protecting instruments.
The place Entrance-Working Occurs Most
1. Decentralized exchanges (DEXs)
DEXs are among the many commonest environments for front-running assaults resulting from their open structure and public mempools. When a person initiates a commerce on DEX platforms, the transaction enters the mempool earlier than being finalized onchain—giving MEV bots time to investigate and exploit the commerce. Bots scan for giant trades or arbitrage alternatives, then submit their very own transactions with increased gasoline charges to get processed first, successfully “slicing the road” and profiting off the slippage created by the sufferer’s order.
2. NFT marketplaces with public bidding
Entrance-running additionally happens on NFT platforms, notably when a high-value bid or itemizing turns into seen earlier than affirmation. Bots or malicious merchants monitor bidding exercise and might rapidly outbid or snatch NFTs earlier than the unique purchaser’s transaction is finalized. For instance, if somebody locations a big bid on a uncommon NFT, an attacker would possibly front-run that bid by providing a barely increased worth with a sooner transaction, snagging the asset earlier than the unique purchaser’s order is processed. This undermines truthful market behaviour and erodes belief in NFT platforms.
3. Token launchpads and preliminary coin choices (ICOs)
Token launchpads and ICOs are hotbeds for front-running in crypto, particularly within the first few moments when a brand new token turns into out there. Bots are programmed to observe good contracts and mempool exercise to allow them to quickly submit purchase orders with extraordinarily excessive gasoline charges, gaining early entry to newly launched tokens. This usually ends in inflated costs earlier than retail customers actually have a probability to take part. By the point unusual traders place their trades, the value might have already spiked considerably, forcing them to purchase at a premium or miss out solely.
How one can Keep away from Entrance-Working in Crypto
1. Use MEV-resistant instruments
To attenuate the chance of front-running and sandwich assaults, think about using MEV-resistant instruments like Flashbots Shield. These instruments provide various transaction submission strategies that bypass the general public mempool—the place malicious bots usually scan for exploitable trades. With Flashbots, customers can ship transaction bundles on to a non-public mempool, maintaining the main points hidden from MEV bots. This safe route helps you keep away from front-runners on DEX platforms. It ensures that your transactions are executed with out being uncovered to opportunistic methods that would manipulate costs or execution timing.
2. Commerce on non-public or protected DEXs
You’ll be able to keep away from front-running through the use of non-public or protected decentralized exchanges like CowSwap and 1inch Fusion implement mechanisms that protect transaction particulars till they’re executed. These platforms act like “darkish swimming pools,” stopping malicious actors from utilizing your commerce information for front-running assaults. By masking your transaction data till it’s too late for others to behave on it, you considerably scale back the chance of manipulation.
3. Set low slippage tolerance
Slippage refers back to the acceptable distinction between the anticipated worth of a commerce and the executed worth. By setting a low slippage tolerance, you restrict how a lot a bot can exploit your transaction by pushing the value in opposition to you. If a bot tries to control the market, your commerce will fail somewhat than execute at a poor fee, defending you from inflated prices.
4. Break massive trades into smaller batches
Executing a big commerce suddenly indicators your intent to the market, making it straightforward for bots to focus on and front-run. As a substitute, breaking it into smaller chunks reduces visibility and the probability of triggering a bot’s algorithm. It additionally smooths out the value affect, guaranteeing your common price stays nearer to market worth.
6. Keep away from buying and selling throughout excessive volatility
Durations of excessive market exercise, reminiscent of throughout information bulletins or main worth swings, entice a swarm of MEV bots seeking to capitalize on chaos. Avoiding trades throughout these risky home windows lowers your possibilities of being front-run, as fewer bots will likely be monitoring your exercise when issues are calmer. Timing is usually a highly effective defence when navigating unpredictable DeFi waters.
Last Ideas
Entrance-running in crypto is a systemic situation deeply tied to blockchain’s open structure. Whereas the visibility of the mempool fosters transparency, it additionally exposes merchants to exploitation. Understanding how front-running works, recognizing its varieties, and utilizing out there instruments and greatest practices may help shield your trades.
Because the DeFi ecosystem matures, we are able to count on larger innovation in MEV mitigation and fairer buying and selling infrastructure. However till then, navigating crypto securely requires consciousness, the correct instruments, and a cautious method.
Disclaimer: This text is meant solely for informational functions and shouldn’t be thought-about buying and selling or funding recommendation. Nothing herein needs to be construed as monetary, authorized, or tax recommendation. Buying and selling or investing in cryptocurrencies carries a substantial threat of monetary loss. All the time conduct due diligence.
If you wish to learn extra market analyses like this one, go to DeFi Planet and observe us on Twitter, LinkedIn, Fb, Instagram, and CoinMarketCap Group.









